Understanding Two-Factor Authentication (2FA)
In an era where cyber threats loom large and digital security is paramount, Two-Factor Authentication (2FA) emerges as a crucial tool to bolster online protection. This authentication method adds an extra layer of security beyond the traditional username-password combination, significantly enhancing the barriers for unauthorized access. Let's delve deeper into what 2FA entails and why it's essential in today's digital landscape.
Posted on 15 Feb 2024
What is Two-Factor Authentication?
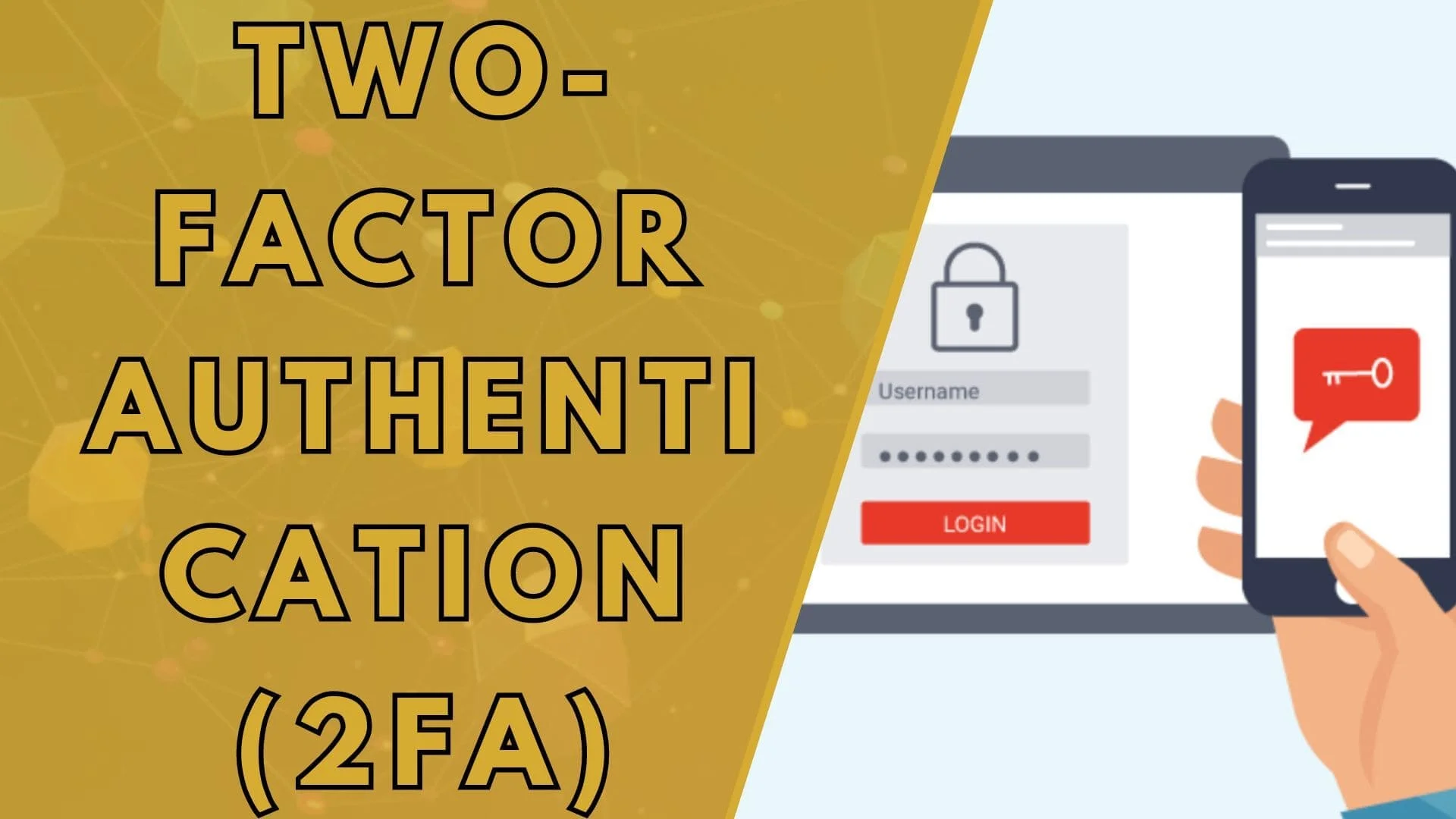
Two-Factor Authentication, commonly abbreviated as 2FA, is a security process that requires users to provide two different authentication factors to verify their identity. These factors typically fall into three categories: something you know, something you have, and something you are.
How Does 2FA Work?
- Something You Know: This factor involves information that only the user should know, such as a password or a personal identification number (PIN).
- Something You Have: This factor refers to a physical item or device that the user possesses, like a smartphone, security token, or smart card.
- Something You Are: This factor involves biometric data unique to the user, such as fingerprints, facial recognition, or voice recognition.
To complete the authentication process, users must provide two of these factors. For instance, a common scenario involves entering a password (something you know) and then confirming a code sent to a mobile device (something you have).
Why is 2FA Important?
- Enhanced Security: By requiring two factors for authentication, 2FA significantly reduces the risk of unauthorized access. Even if one factor (like a password) is compromised, the attacker would still need the second factor to gain entry.
- Protection Against Password Theft: Passwords are vulnerable to theft through various means, including phishing attacks, malware, and data breaches. 2FA mitigates the impact of password theft by adding an additional layer of verification.
- Compliance Requirements: Many industries and regulatory standards mandate the use of multi-factor authentication to safeguard sensitive data. Adhering to these requirements helps organizations avoid potential legal and financial consequences.
- User Confidence: Implementing 2FA reassures users that their accounts are better protected, fostering trust and confidence in the platform or service.
Types of 2FA
- SMS-based Authentication: In this method, a one-time code is sent via text message to the user's mobile phone.
- Authentication Apps: Specialized mobile apps, such as Google Authenticator or Authy, generate time-based or event-based codes that users must enter for authentication.
- Biometric Authentication: This method uses unique biological traits, such as fingerprints or facial features, for identity verification.
- Hardware Tokens: Physical devices, like USB security keys or smart cards, provide a secondary authentication factor.
Conclusion:
In an age marked by escalating cyber threats, Two-Factor Authentication stands as a critical safeguard against unauthorized access and data breaches. By requiring users to verify their identity through multiple factors, 2FA adds an invaluable layer of protection to online accounts and systems. As technology evolves and security risks evolve with it, the adoption of robust authentication measures like 2FA becomes increasingly indispensable in fortifying digital defenses and preserving user trust.